The Ultimate Guide to Client and Secret
Welcome to the definitive guide on the fascinating world of Client and Secret, a crucial aspect of modern digital security and authentication. In today's interconnected world, the need for robust security measures is paramount, and understanding the intricacies of Client and Secret is essential for developers, security experts, and anyone involved in building and safeguarding online systems. This comprehensive guide aims to provide an in-depth exploration of Client and Secret, covering its history, applications, best practices, and future prospects.
Unraveling the Secrets of Client and Secret

Client and Secret, often referred to as Client Credentials, are integral components of the OAuth 2.0 authorization framework, which has become the standard for secure access control in web and mobile applications. The concept of Client and Secret is a cornerstone of modern authentication, providing a robust mechanism to ensure that only authorized entities can access protected resources.
The Anatomy of Client and Secret
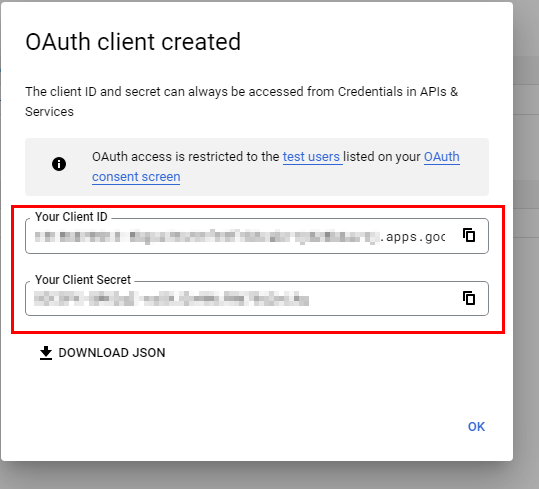
At its core, the Client and Secret mechanism involves two unique identifiers: the Client ID and the Client Secret. The Client ID is a publicly accessible identifier that identifies the client application or service. It is typically a unique alphanumeric string that is issued by the authorization server during the registration process. On the other hand, the Client Secret is a confidential credential that is known only to the client and the authorization server. It is used to prove the client’s identity and to ensure that the client is authorized to access the protected resources.
| Component | Description |
|---|---|
| Client ID | A unique identifier for the client application, publicly accessible. |
| Client Secret | A confidential credential, known only to the client and the authorization server, used for authentication. |
The combination of the Client ID and the Client Secret forms the foundation of the Client Credentials Grant Type, one of the core grant types defined in OAuth 2.0. This grant type allows the client to directly authenticate itself to the authorization server, making it suitable for machine-to-machine communication and scenarios where the client does not have a user interface to interact with.
The Client Credentials Grant Type
The Client Credentials Grant Type is a straightforward and efficient method for obtaining an access token. The client sends its Client ID and Client Secret to the authorization server, typically via a HTTP POST request. The authorization server then validates these credentials and, if they are valid, issues an access token to the client. This access token can then be used by the client to access protected resources on behalf of the client itself, rather than on behalf of a specific user.
The access token issued by the authorization server is a JSON Web Token (JWT) that contains various claims, including the client's identity, the scope of access granted, and an expiration time. This token is typically short-lived, ensuring that the access is temporary and must be regularly refreshed to maintain security.
Real-World Applications
The Client and Secret mechanism, and specifically the Client Credentials Grant Type, finds extensive use in various real-world scenarios. Some common applications include:
- Machine-to-Machine Communication: In scenarios where machines or services need to communicate directly with each other, such as in IoT devices or server-to-server interactions, the Client Credentials Grant Type provides a secure and efficient way to authenticate these interactions.
- API Access: Many web services and APIs use OAuth 2.0 and the Client Credentials Grant Type to control access to their resources. Developers can register their applications and obtain Client IDs and Secrets to integrate with these services securely.
- Data Integration: When different systems or databases need to share data, the Client Credentials Grant Type can be used to establish a secure connection and allow the exchange of data without exposing sensitive user credentials.
- Automated Processes: In scenarios where automated tasks or scripts need to access protected resources, such as in backup systems or data synchronization processes, the Client Credentials Grant Type offers a straightforward solution.
Best Practices and Security Considerations

While the Client and Secret mechanism provides a robust authentication framework, it is crucial to adhere to best practices and security guidelines to ensure the integrity and confidentiality of the credentials. Here are some key considerations:
Secure Storage and Transmission
The Client Secret should be stored securely and never exposed in plain text. It should be encrypted at rest and transmitted over secure channels, such as HTTPS. Additionally, the Client Secret should be treated as a sensitive credential and should not be shared or exposed to unauthorized parties.
Regular Rotation
Just like passwords, Client Secrets should be regularly rotated to minimize the risk of compromise. The rotation frequency can depend on the sensitivity of the resources being protected and the organization’s security policies. It is recommended to implement a scheduled rotation process to ensure that secrets are refreshed periodically.
Access Control
The Client Credentials Grant Type allows the client to access resources on its own behalf, so it is essential to define and enforce access control policies. This includes specifying the scope of access granted to each client, ensuring that clients can only access the resources they require for their intended purpose.
Monitoring and Logging
Implement robust monitoring and logging mechanisms to track the usage of Client and Secret. This includes logging all access attempts, successful and failed, to detect any suspicious activity. Regularly reviewing these logs can help identify potential security breaches or misuse of credentials.
Secure Development Practices
Developers should follow secure coding practices when implementing the Client Credentials Grant Type. This includes using libraries and frameworks that provide secure implementations of OAuth 2.0, properly handling errors and exceptions, and avoiding common security pitfalls such as hardcoding credentials or exposing them in error messages.
The Future of Client and Secret
As technology evolves and security threats become more sophisticated, the field of authentication and access control continues to innovate. While the Client and Secret mechanism, as defined in OAuth 2.0, remains a cornerstone of secure authentication, there are ongoing efforts to enhance and adapt this framework to meet the changing security landscape.
Emerging Trends
One notable trend is the increasing adoption of more advanced grant types, such as the Authorization Code Grant Type and the Implicit Grant Type. These grant types offer additional security measures and are suitable for different use cases, particularly those involving user interaction and delegation of access.
Additionally, the rise of zero-trust security models and the shift towards more granular access control policies are shaping the future of authentication. This includes the adoption of dynamic access control, where access decisions are made based on real-time context and risk assessment, rather than static credentials.
Industry Innovations
Industry leaders and security experts are actively working on enhancing the OAuth 2.0 framework and developing new protocols to address emerging security challenges. These efforts include:
- OAuth 3.0: While still in development, OAuth 3.0 aims to address some of the limitations of the current OAuth 2.0 specification, particularly in terms of scope management and consent handling.
- OpenID Connect: This is a layer on top of OAuth 2.0 that adds identity capabilities, allowing clients to verify the identity of users and obtain basic profile information.
- Device Flow: This is a grant type introduced in OAuth 2.0 that enables access for clients with limited input capabilities, such as smart TVs or IoT devices.
Looking Ahead
As we move forward, the field of authentication and access control will continue to evolve, driven by advancements in technology and the need to stay ahead of evolving security threats. The Client and Secret mechanism, as a fundamental component of OAuth 2.0, will remain a critical aspect of secure authentication, while also adapting to meet the challenges of the future.
Conclusion
In conclusion, the Client and Secret mechanism, as defined by OAuth 2.0, provides a robust and efficient framework for secure authentication and access control. By understanding its history, applications, and best practices, developers and security professionals can leverage this powerful tool to build secure and reliable systems. As the digital landscape evolves, staying informed about emerging trends and industry innovations will be key to maintaining the integrity and security of online systems.
What is the primary purpose of the Client and Secret mechanism in OAuth 2.0?
+The Client and Secret mechanism, also known as the Client Credentials Grant Type, allows a client application to directly authenticate itself to the authorization server, enabling it to access protected resources on its own behalf. This grant type is particularly useful in machine-to-machine communication and scenarios where the client does not have a user interface.
How should Client Secrets be stored and transmitted securely?
+Client Secrets should be stored encrypted at rest and transmitted over secure channels, such as HTTPS. They should never be exposed in plain text or shared with unauthorized parties. Secure storage and transmission are critical to maintaining the confidentiality and integrity of the credentials.
What are some real-world applications of the Client Credentials Grant Type?
+The Client Credentials Grant Type finds extensive use in various scenarios, including machine-to-machine communication, API access, data integration, and automated processes. It provides a secure and efficient way for machines or services to communicate and access resources directly, without involving user credentials.