Kick Them Offline: 5 Methods
In today's interconnected world, where digital connectivity is paramount, the ability to disrupt an opponent's online presence has become a strategic advantage in various fields. Whether it's a gaming tournament, a competitive online event, or even a cybersecurity scenario, understanding the methods to "kick someone offline" is an essential skill. This article delves into five effective techniques to achieve this, offering a comprehensive guide for those seeking a tactical edge in their digital endeavors.
1. Distributed Denial of Service (DDoS) Attacks

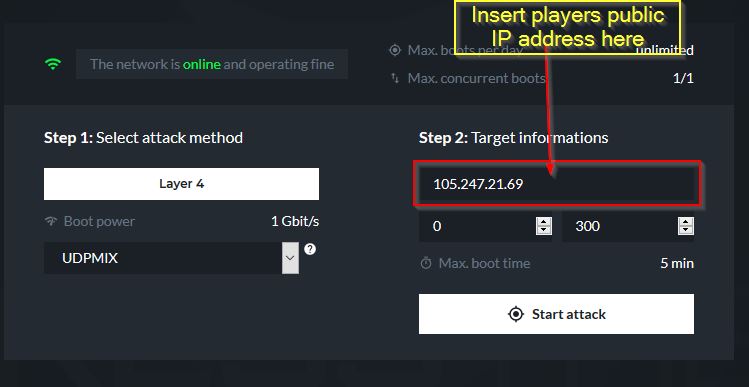
One of the most notorious methods to disrupt online activity is through Distributed Denial of Service (DDoS) attacks. These attacks aim to overwhelm a target’s network or server with an excessive amount of traffic, rendering it inaccessible to legitimate users. The key to a successful DDoS attack lies in the distribution of the traffic across multiple sources, making it challenging to identify and mitigate.
There are several types of DDoS attacks, each targeting a specific aspect of a network's infrastructure. For instance, a volumetric attack floods the target with a massive volume of data, consuming all available bandwidth. On the other hand, a protocol attack exploits vulnerabilities in network protocols, potentially causing a server to crash. Finally, an application layer attack targets specific web applications, disrupting services like e-commerce platforms or social media sites.
While DDoS attacks can be powerful, they are often illegal and unethical. It's crucial to approach this method with caution and a deep understanding of the potential consequences. Furthermore, advancements in cybersecurity have led to the development of robust DDoS protection systems, making this method increasingly difficult to execute successfully.
Mitigation Strategies for DDoS Attacks
For those seeking to protect their online infrastructure from DDoS attacks, several strategies can be employed:
- DDoS Protection Services: Utilizing specialized services that monitor and mitigate DDoS attacks can be an effective solution. These services often employ advanced traffic analysis techniques to identify and block malicious traffic.
- Traffic Filtering: Implementing robust traffic filtering mechanisms can help identify and block excessive or suspicious traffic, reducing the impact of DDoS attacks.
- Network Redundancy: Building redundancy into network infrastructure can ensure that even if one route is overwhelmed, alternative paths are available to maintain connectivity.
2. IP Spoofing and Packet Manipulation

IP Spoofing is a technique where an attacker disguises their IP address, making it appear as though the traffic is originating from a trusted source. This method can be used to bypass security measures and gain unauthorized access to a network. By manipulating packets, an attacker can also disrupt the normal flow of data, potentially causing a denial of service.
One common approach is to send a flood of ICMP (Internet Control Message Protocol) packets, commonly known as "ping" requests, to a target system. This can overwhelm the target's resources, leading to a temporary denial of service. Additionally, an attacker might exploit vulnerabilities in network protocols, such as TCP/IP, to manipulate packet headers and disrupt the normal functioning of a network.
Defending Against IP Spoofing
Protecting against IP spoofing requires a multi-layered approach:
- Network Access Control: Implementing strict access control measures can help ensure that only authorized devices can connect to the network. This can involve the use of authentication protocols and regular security audits.
- Intrusion Detection Systems (IDS): Deploying IDS can help identify and mitigate suspicious activities, including IP spoofing attempts.
- Packet Filtering: Employing advanced packet filtering techniques can help identify and block malicious packets, reducing the impact of IP spoofing attacks.
3. Network Congestion and Overload
Overloading a network with excessive traffic or resource-intensive activities can lead to congestion and, ultimately, a denial of service. This method leverages the inherent limitations of network infrastructure, where excessive demand can lead to slowdowns and connectivity issues.
For instance, in a gaming context, an attacker might initiate multiple resource-intensive processes on their device, intentionally causing network congestion. This can disrupt the gaming experience for other players, potentially leading to disconnections.
Network Optimization Strategies
To mitigate the risk of network congestion and overload, network administrators can implement the following measures:
- Bandwidth Management: Implementing bandwidth throttling and prioritization can ensure that critical services receive adequate resources, even during periods of high demand.
- Network Monitoring: Continuous monitoring of network traffic and resource utilization can help identify potential bottlenecks and congestion points, allowing for proactive measures.
- Network Segmentation: Dividing a network into smaller segments can help isolate issues and prevent the spread of congestion across the entire infrastructure.
4. Exploiting Network Vulnerabilities
Identifying and exploiting vulnerabilities in a target’s network infrastructure can be a powerful method to disrupt online activity. This approach requires a deep understanding of network protocols and potential security gaps.
For example, an attacker might exploit a vulnerability in a router's firmware, allowing them to gain remote access and disrupt network connectivity. Similarly, vulnerabilities in network-attached storage (NAS) devices can be exploited to disrupt file sharing and collaboration.
Vulnerability Management and Patching
To protect against network vulnerabilities, it’s crucial to adopt a proactive approach:
- Regular Security Audits: Conducting frequent security audits can help identify potential vulnerabilities and weaknesses in the network infrastructure.
- Patch Management: Keeping all network devices and software up-to-date with the latest security patches is essential to mitigate known vulnerabilities.
- Security Training: Educating network administrators and users about potential threats and best practices can help reduce the risk of successful attacks.
5. Physical Interference

In some cases, disrupting an opponent’s online activity can be as simple as causing physical interference with their network infrastructure. This might involve cutting network cables, disrupting power supply, or even jamming wireless signals.
While this method can be effective in certain scenarios, it often requires physical access to the target's infrastructure, making it less practical in many situations. Additionally, the legal and ethical implications of such actions should not be underestimated.
Network Security Best Practices
To minimize the risk of physical interference, consider the following practices:
- Physical Security: Implementing robust physical security measures, such as access controls and surveillance, can help deter potential attackers.
- Redundancy and Backup: Ensuring that critical network components have backups or redundant systems can help maintain connectivity even in the face of physical interference.
- Regular Maintenance: Conducting regular maintenance checks can help identify potential physical issues, such as damaged cables or power supply problems.
How can I protect my network from DDoS attacks?
+Protecting your network from DDoS attacks requires a comprehensive approach. This includes investing in DDoS protection services, implementing robust traffic filtering mechanisms, and building redundancy into your network infrastructure. Regular security audits and proactive monitoring can also help identify potential vulnerabilities.
Are there legal consequences for conducting DDoS attacks?
+Yes, DDoS attacks are illegal in most jurisdictions. Conducting such attacks can result in severe legal consequences, including fines and imprisonment. It’s crucial to understand the ethical and legal boundaries when considering any disruptive online tactics.
How can I mitigate the risk of IP spoofing on my network?
+To mitigate IP spoofing, implement strict network access control measures, deploy Intrusion Detection Systems (IDS), and employ advanced packet filtering techniques. Regular security audits and user education can also help identify and prevent potential IP spoofing attempts.



