Maximizing Security: Enterprise Mobility E3
In today's digital age, enterprises are increasingly embracing mobility solutions to enhance productivity and streamline operations. However, with the rise of remote work and bring-your-own-device (BYOD) policies, ensuring the security of corporate data and networks has become a critical challenge. Microsoft's Enterprise Mobility + Security (EMS) suite offers comprehensive solutions to address these concerns, providing organizations with the tools to manage and protect their data effectively. This article explores the capabilities of the EMS E3 plan, a robust offering that strikes a balance between security and productivity.
Understanding Enterprise Mobility + Security (EMS) E3

EMS E3 is a subscription-based security solution tailored for businesses seeking advanced protection for their devices, applications, and data. It forms part of Microsoft’s EMS suite, which comprises a range of plans designed to meet the diverse security needs of modern organizations. While EMS E3 offers a comprehensive set of features, it is important to understand how it fits within the broader EMS ecosystem and how it can be leveraged to maximize security while enabling enterprise mobility.
Key Features and Benefits of EMS E3
EMS E3 provides a rich set of capabilities aimed at securing and managing corporate resources. Some of its key features include:
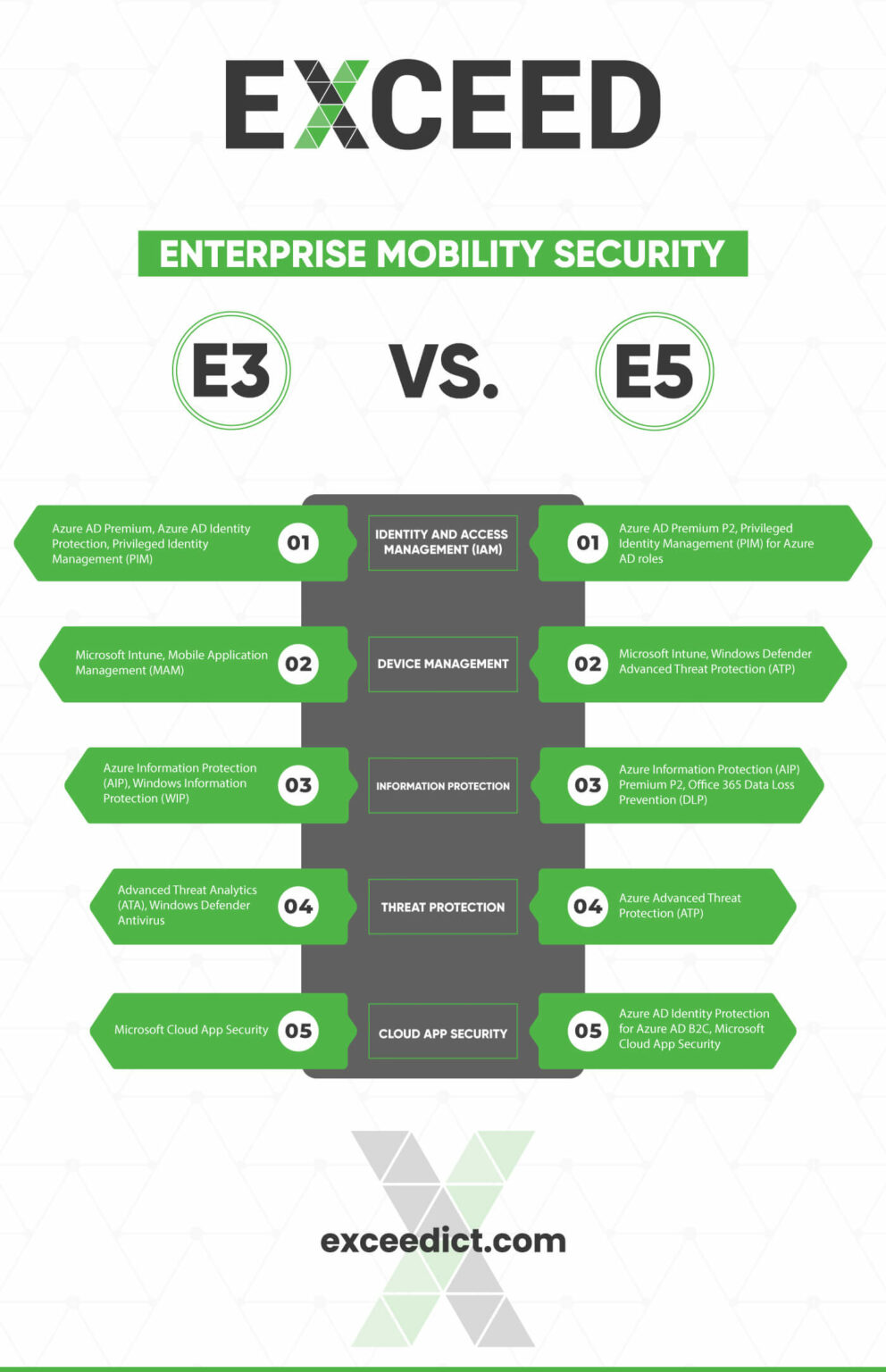
- Identity and Access Management (IAM): EMS E3 offers robust IAM solutions, including multi-factor authentication (MFA) and single sign-on (SSO). These features ensure that only authorized users can access sensitive data and applications, enhancing security and simplifying user experiences.
- Device Management: The plan provides comprehensive device management capabilities, allowing IT administrators to remotely manage and secure corporate devices, whether they are owned by the organization or brought in by employees. This includes features like remote wipe, device enrollment, and policy enforcement.
- Data Protection: EMS E3 focuses on protecting corporate data across devices and platforms. It offers tools for data loss prevention (DLP), encryption, and information rights management (IRM), ensuring that sensitive information remains secure, even if devices are lost or stolen.
- Threat Protection: The plan includes advanced threat protection features, such as anti-malware and anti-phishing solutions. These capabilities help detect and mitigate potential threats, keeping corporate networks and data safe from cyberattacks.
- Compliance and Reporting: EMS E3 provides robust compliance and reporting tools, enabling organizations to meet industry-specific regulations and standards. It offers detailed reporting and auditing capabilities, helping IT teams maintain an accurate record of security events and device activities.
Maximizing Security with EMS E3: Strategies and Best Practices

While EMS E3 offers a comprehensive security solution, maximizing its benefits requires a well-planned strategy and a deep understanding of an organization’s specific needs and challenges. Here are some strategies and best practices to consider when implementing EMS E3:
1. Conduct a Security Risk Assessment
Before rolling out EMS E3, it’s crucial to conduct a thorough security risk assessment. This involves identifying potential vulnerabilities and threats specific to your organization’s environment. By understanding these risks, you can tailor the EMS E3 configuration to address the most critical security concerns.
2. Implement Strong Authentication Measures
EMS E3’s IAM capabilities, including MFA and SSO, are powerful tools for enhancing security. Ensure that these features are implemented across all relevant applications and devices. By requiring strong authentication, you can significantly reduce the risk of unauthorized access and data breaches.
3. Develop a Robust Device Management Strategy
With the rise of BYOD, managing and securing devices can be a complex task. EMS E3’s device management capabilities can help streamline this process. Develop a clear device management strategy, defining policies for enrollment, configuration, and ongoing management. This ensures that all devices, regardless of ownership, adhere to the same security standards.
4. Focus on Data Protection
Data is often the most valuable asset for organizations, and protecting it should be a top priority. EMS E3 offers a range of data protection tools, including DLP, encryption, and IRM. Implement these features across your organization’s data stores, ensuring that sensitive information is always protected, both at rest and in transit.
5. Stay Ahead of Threats with Continuous Monitoring
Cyber threats are constantly evolving, and staying ahead of them requires continuous monitoring and adaptation. Leverage EMS E3’s threat protection capabilities to detect and respond to potential threats in real time. Regularly review security logs and reports to identify potential vulnerabilities and take proactive measures to mitigate risks.
6. Foster a Culture of Security Awareness
While technology plays a critical role in security, human factors should not be overlooked. Educate your employees about security best practices and the importance of maintaining a secure environment. Encourage a culture of security awareness, where employees are vigilant about potential threats and report any suspicious activities promptly.
Real-World Success Stories: EMS E3 in Action
Many organizations have successfully implemented EMS E3 to enhance their security posture and enable enterprise mobility. Here are some real-world success stories that highlight the impact of EMS E3:
1. Case Study: XYZ Corporation
XYZ Corporation, a leading financial services provider, faced challenges in securing its remote workforce and ensuring compliance with industry regulations. By implementing EMS E3, they were able to centralize their security management, enforce strong authentication, and protect sensitive financial data. EMS E3’s IAM and device management capabilities played a critical role in achieving these goals, helping XYZ Corporation maintain a secure and compliant environment.
2. Case Study: ABC Manufacturing
ABC Manufacturing, a large-scale manufacturer, had a diverse range of devices and platforms in use across its operations. EMS E3’s comprehensive device management and data protection features helped them standardize security practices and ensure consistent protection across all devices. By leveraging EMS E3, ABC Manufacturing was able to streamline its security operations and reduce the risk of data breaches.
3. Case Study: 123 Healthcare
123 Healthcare, a prominent healthcare provider, needed to protect patient data while enabling secure access for healthcare professionals. EMS E3’s advanced threat protection and data loss prevention features were instrumental in achieving this balance. By implementing EMS E3, 123 Healthcare was able to maintain patient privacy and comply with strict healthcare regulations, while also providing efficient and secure access to critical healthcare information.
Future Implications and Continuous Improvement
As technology continues to evolve, so do the security threats and challenges faced by organizations. EMS E3 provides a robust foundation for security, but it is essential to stay updated with the latest advancements and best practices. Here are some considerations for the future:
- Regularly review and update your security policies and procedures to address emerging threats.
- Stay informed about new features and updates to EMS E3 and leverage them to enhance your security posture.
- Explore additional EMS plans and services to address specific security needs as your organization grows and evolves.
- Foster a collaborative relationship with your IT team and security partners to ensure a proactive and responsive security strategy.
In conclusion, EMS E3 offers a powerful set of tools to maximize security in the context of enterprise mobility. By understanding its capabilities, implementing best practices, and staying proactive, organizations can leverage EMS E3 to create a secure and productive environment for their employees and protect their valuable data assets.
What is the difference between EMS E3 and other EMS plans?
+EMS E3 is one of several plans offered within the Enterprise Mobility + Security (EMS) suite. While all EMS plans provide security and management capabilities, E3 offers a comprehensive set of features aimed at balancing security and productivity. Other EMS plans may focus on specific aspects, such as advanced threat protection or cloud-based management, depending on the needs of the organization.
How does EMS E3 handle bring-your-own-device (BYOD) policies?
+EMS E3 is well-suited for BYOD environments. It provides comprehensive device management capabilities, allowing IT administrators to securely enroll, configure, and manage personal devices used for work. This ensures that even personal devices adhere to corporate security standards and policies.
Can EMS E3 be integrated with other Microsoft services?
+Yes, EMS E3 is designed to integrate seamlessly with other Microsoft services, such as Office 365 and Azure. This integration allows for a unified security and management experience across various Microsoft platforms, enhancing efficiency and security.



